iOT365 Redefines OT Cybersecurity With Passive Asset Discovery and AI-Powered CVE Intelligence
New York, NY – December 4, 2025
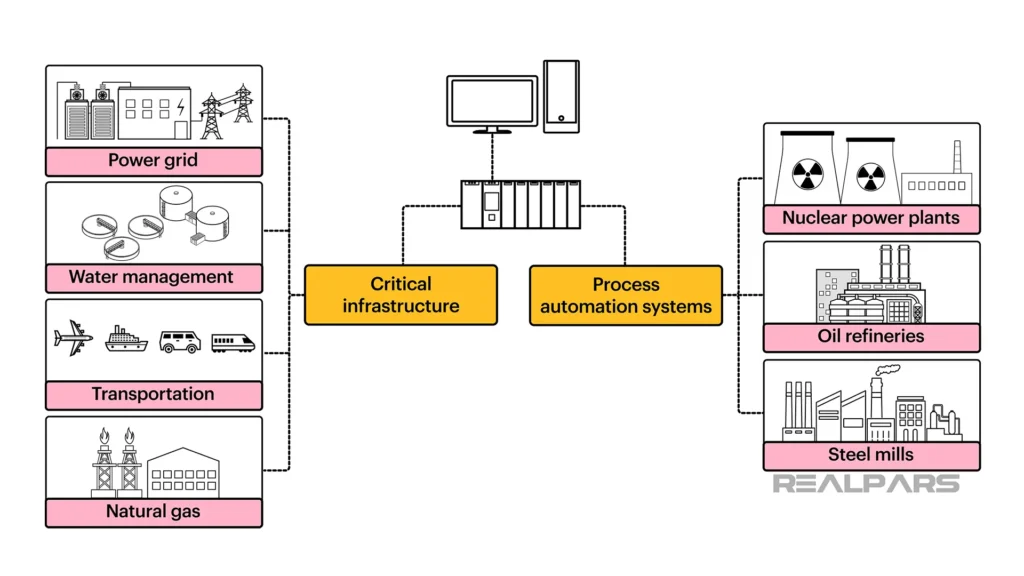
Industrial networks are more connected and more exposed than ever. To close the gap, iOT365 has launched the first passive OT asset discovery engine with AI-driven firmware visibility and integrated CVE intelligence, fully tied into its in-house SOC platform.
This launch creates a unified asset-discovery-to-SOC chain, giving critical infrastructure operators a single view of every device, its firmware, and its vulnerabilities—even in isolated or highly segmented environments.
A Complete Asset-to-SOC Visibility Chain
Traditional OT security tools often focus on one slice of the problem. They discover assets, or they monitor traffic, or they manage alerts. iOT365 combines these functions into a single, in-house platform. From first discovery to SOC-level response, each step is integrated and powered by the same AI-driven intelligence.
According to the company, this unified approach delivers:
- Passive discovery of every OT asset, from PLCs and RTUs to HMIs, sensors, and micro-devices
- Automatic firmware version detection for deep visibility at the device level
- AI-powered scoring of CVE exposure, mapped directly to SOC workflows
- End-to-end visibility across isolated, hybrid, and highly segmented networks
Eliminating Blind Spots in Critical Infrastructure
One of the biggest challenges in OT security is the number of blind spots that legacy tools miss. Devices may be connected but invisible. Firmware may be outdated but unmanaged. Vulnerabilities may exist but remain unprioritized.
iOT365’s passive engine is designed to remove those gaps. It continuously maps each asset, tracks its firmware, and correlates known vulnerabilities with real-time SOC data. As a result, security teams can see where their highest risks are and respond much faster.
Protocol-Level Intelligence for OT Environments
OT networks depend on specialized protocols that most IT tools simply do not understand. iOT365’s discovery engine natively reads key industrial protocols such as Modbus, S7, CIP, BACnet, Profinet, DNP3, and IEC-104, among others. This protocol-level intelligence allows the platform to fingerprint devices with high accuracy while remaining completely passive.
Vendor-agnostic PLC interrogation, zero-touch discovery, and AI-generated CVSS/CVE scoring all feed into iOT365’s SOC correlation layer. Because of this, teams can monitor risk without disrupting production or interfering with sensitive controllers.
Built for Global Compliance and Industrial Standards
Regulatory pressure on critical infrastructure is increasing around the world. iOT365 aligns its platform with major industrial-cyber frameworks, including:
- NIS2 Directive (EU)
- NIST Cybersecurity Framework and NIST 800-53
- IEC 62443 and NERC CIP for industrial control systems
- MITRE ATT&CK for ICS
- ISO 27001 and other global security standards
Because the platform is built with compliance in mind, organizations can simplify reporting, streamline audits, and demonstrate continuous monitoring across their OT environments.
Global Deployment Footprint
iOT365 has already deployed its unified OT/IoT cybersecurity stack across sectors such as energy, water, manufacturing, transportation, airports, and building management systems. The platform includes AI-powered IDS, a next-generation SIEM for OT + IoT, and a full SOC with automated playbooks and compliance mapping.
This broad deployment footprint positions iOT365 as a backbone for modern critical infrastructure, enabling operators to scale protection as their networks grow.
Leadership Vision and the Future of OT Security
iOT365’s leadership envisions a future where organizations have complete control over their cybersecurity chain—from the shop floor and field devices all the way up to the SOC. By keeping detection, intelligence, and response fully in-house, the company aims to reduce dependence on third-party tools and close blind spots faster.
The launch of the passive OT asset discovery engine is a major step toward that vision. With firmware-aware visibility, AI-driven CVE intelligence, and end-to-end SOC integration, operators can move from reactive defense to proactive, data-driven protection.
Learn More About the Announcement
To read the original press release, visit the coverage on EIN Presswire, or learn more about the iOT365 OT/IoT cybersecurity platform at iot365.io.